White Smartphone with Fingerprint Scanner Icon Isolated with Long Shadow. Concept of Security, Personal Access Via Stock Vector - Illustration of touch, circle: 216394590
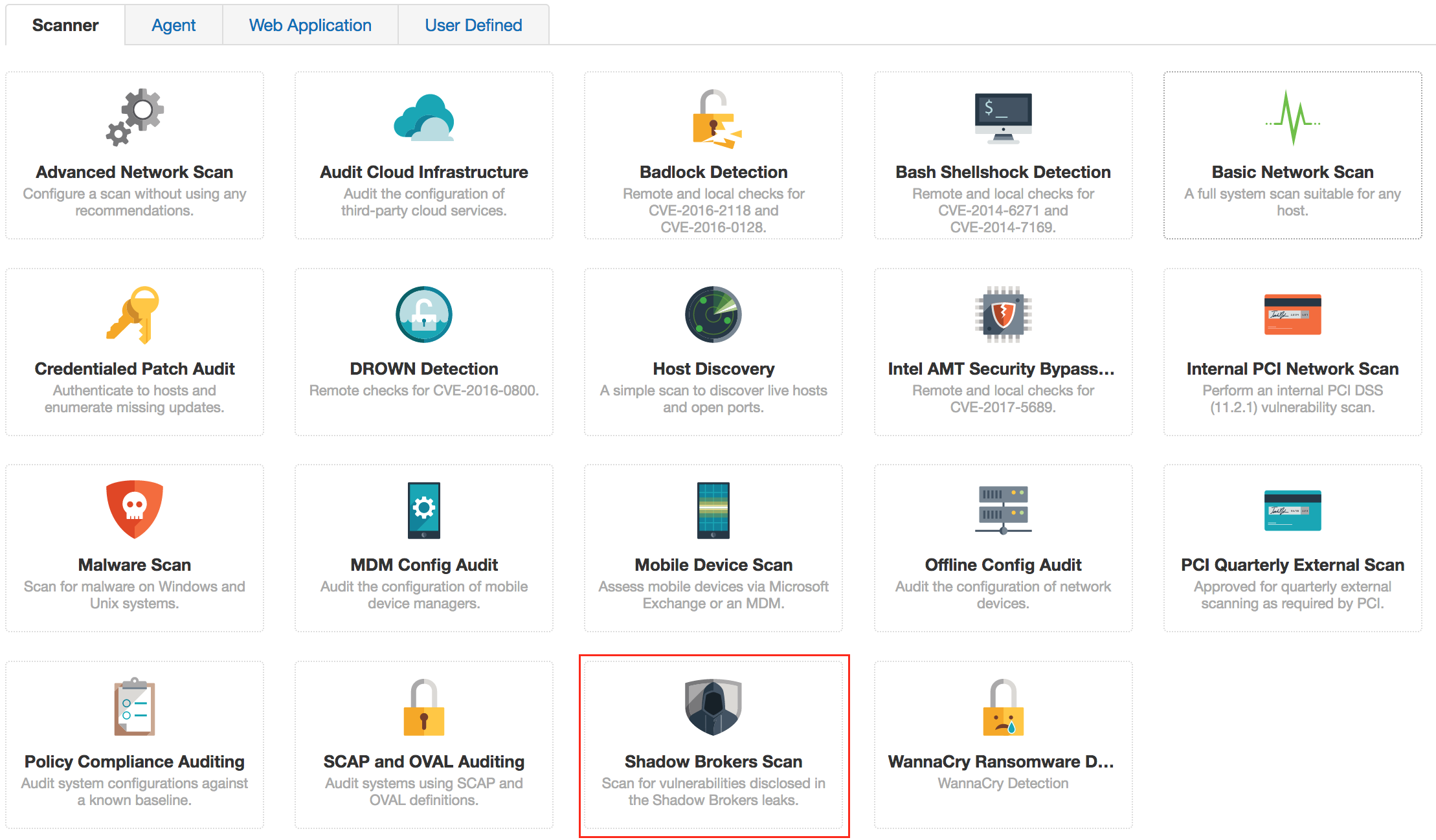
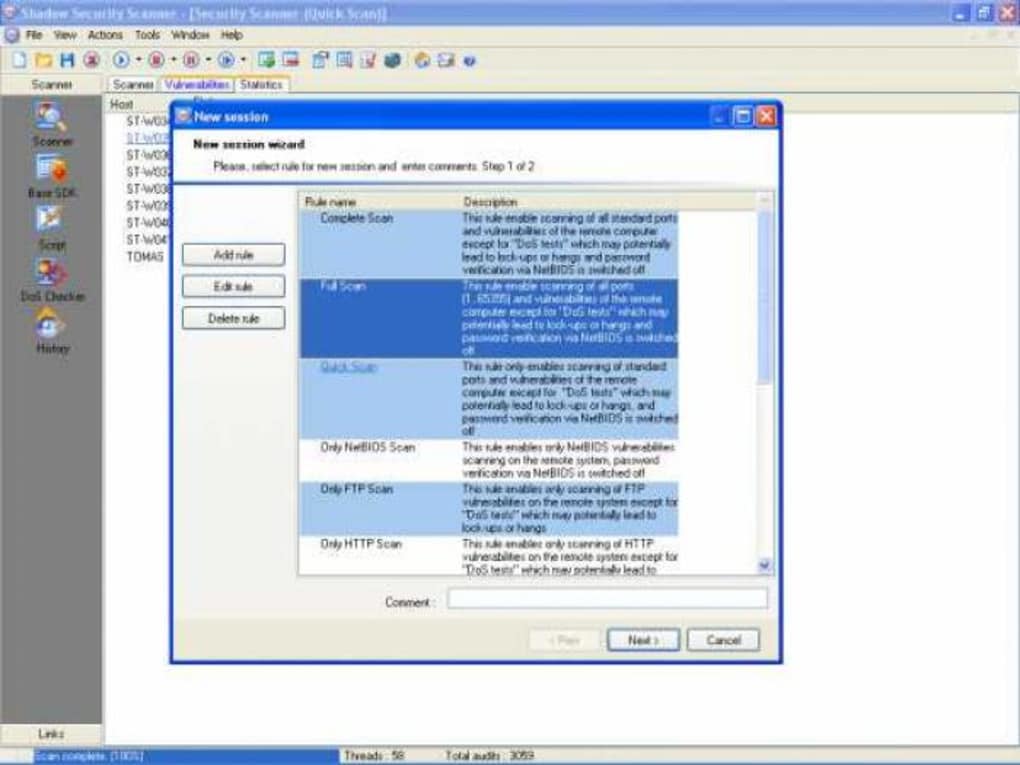
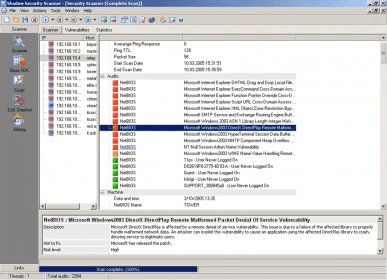
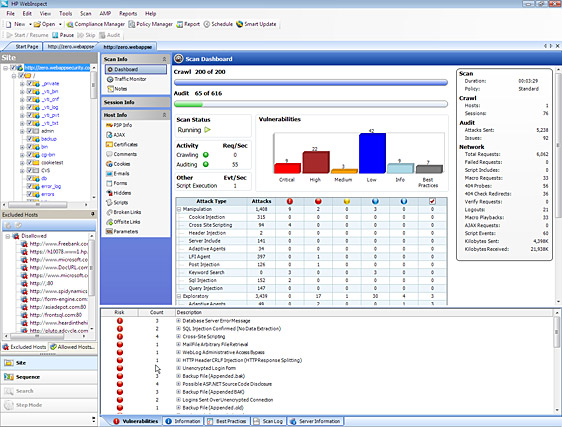
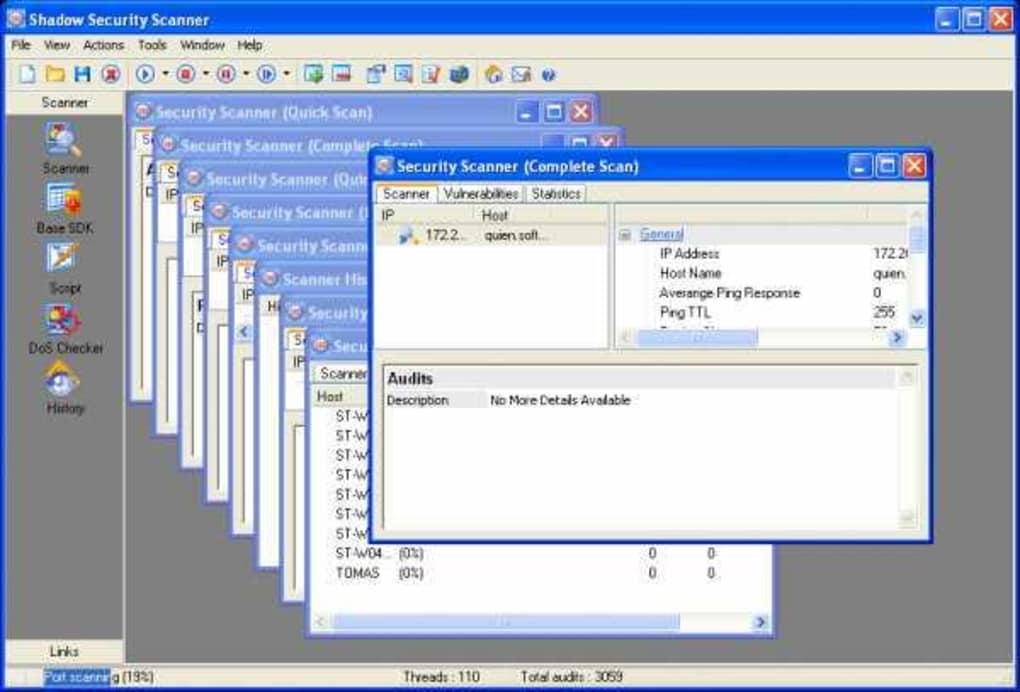
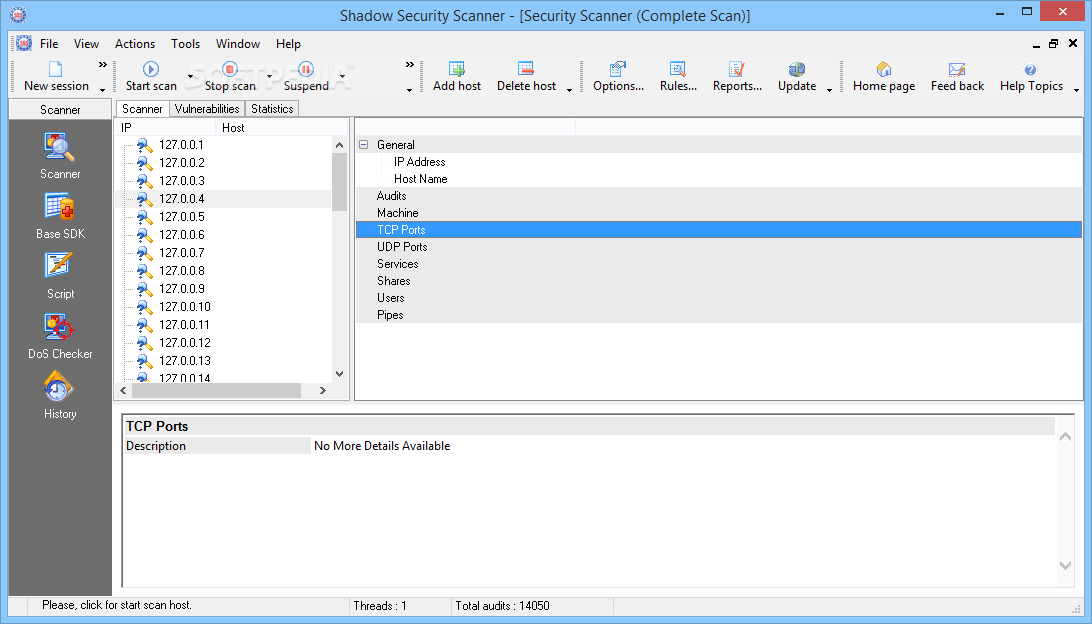
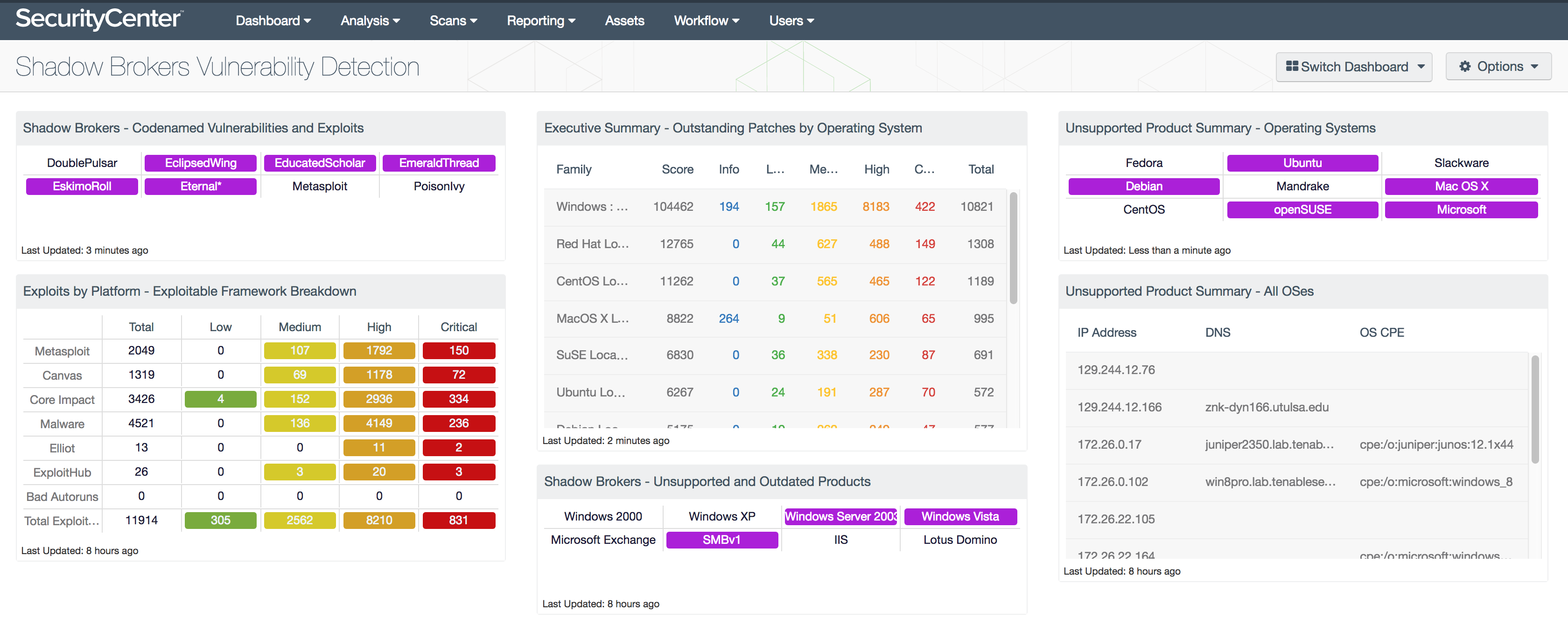
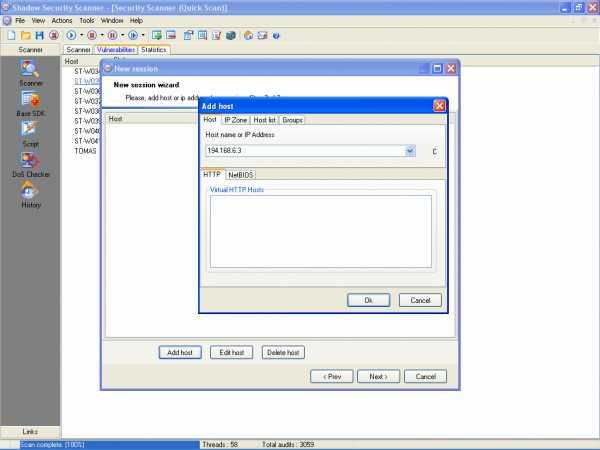
Shadow Database Scanner Download - It provides a secure and prompt detection of security system holes
Airport Baggage Security Scanner Icon, Flat Style Stock Vector - Illustration of airport, crime: 83184275
White Line Face Recognition Icon Isolated With Long Shadow Face Identification Scanner Icon Facial Id Cyber Security Concept Green Square Button Vector Stock Illustration - Download Image Now - iStock
White Face Recognition Icon Isolated With Long Shadow Face Identification Scanner Icon Facial Id Cyber Security Concept Green Circle Button Vector Illustration Stock Illustration - Download Image Now - iStock